Cross Site Request Forgery
Contents
Background Information
- Damn Vulnerable Web App(DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and aid teachers/students to teach/learn web application security in a class room environment.
- CSRF is an attack which forces an end user to execute unwanted actions on a web application in which he/she is currently authenticated. With a little help of social engineering (like sending a link via email/chat), an attacker may force the users of a web application to execute actions of the attacker's choosing. A successful CSRF exploit can compromise end user data and operation in case of normal user. If the targeted end user is the administrator account, this can compromise the entire web application.
Login and Set Security Setup
- Login to Damn Vulnerable Web App:
- Start up FireFox
- Place http://127.0.0.1/dvwa/login.php in the address bar
- Input Username: admin and Password: password
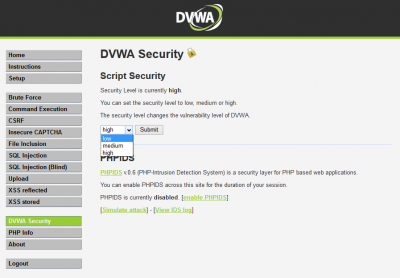
- Set DVWA Security Level:
- Click on DVWA Security, in the left hand menu.
- Select “low” and click Submit
Basic Cross Site Request Forgery Test
- Instructions:
- Select “CSRF” from the left navigation menu.
- Input New password: abc123
- Confirm new password: abc123
- Click Change
- Notes:
- Below the change button you will notice the message that says “Password Changed.”
- notice The is the URL string in the address bar.
- See how the URL string has the below two parameters separated by a “&”.
- password_new=abc123
- password_conf=abc123
- This is DVWA's example of bad implementation of how to change a password on a web application for the following reasons:
- http is being used instead of https, which means this password change was in clear text.
- An attacker could manipulate the URL string using the address bar to change the password.
Address Bar CSRF Test
- Instruction:
- In the URL, after password_new=, replace abc123 with test123.
- In the URL, after password_conf=, replace abc123 with test123.
- Click the Reload Current Page Arrow
- Notes:
- Notice the password is changed.
- Using cookie string and URL string the attacker will be able to change the password remotely without a browser.
References
Panel title
Percipit Mnesarchum
Molestie Phaedrum Luptatum
constituam Habeo adipisci Inani
zril Forensibus sea Habeo
adipisci Minimum corrumpit Regione
suscipit Has et partem Percipit
Mnesarchum Molestie Phaedrum
Luptatum constituam Habeo
adipisci Inani zril Vel
nisl albucius Habeo adipisci Minimum
corrumpit Regione suscipit Percipit
maiestatis Regione suscipit Percipit
maiestatis
Subtitle