BackTrack Penetration Testing
Contents
Introduction
- Penetration testing is a legal and authorized attempt to exploit computer systems for the purpose of making the computer systems more secure.
- Backtrack is the best penetration testing distribution. Offers some penetration testing programs and these programs will used in this Backtrack Penetration Testing Tutorial.
- The results of penetration testing are addressing the vulnerabilities in the computer system and also particular recommendations for fixing the vulnerabilities. Penetration testing is used to protect the computer systems and networks from attackers (Black Hat Hacker).
Requirements
- You need a place to practice this Backtrack Penetration Testing Tutorial. Virtual Lab is the solutions. You can make a network in your own computer without “real computer”. With virtual lab you can practice without harming other computer systems. Virtual Machine is the solution. With Virtual Machine you can install OS under your OS, in other words you can use multiple OS in the same time and in the same machine.
- There are some Virtualization software, for example VirtualBox and VMware. But I recommended VirtualBox for this Backtrack Penetration Testing Tutorial. You can install VirtualBox on your Backtrack for free because VirtualBox is an Open Source software.
Backtrack Penetration Testing Tutorial
- This Backtrack Penetration Testing Tutorial is a penetration testing tutorial using Backtrack Linux.
Step 1 : Information Gathering
- The first step of Backtrack Penetration Testing Tutorial is Information Gathering. Gathering all of the information from the web about victim. If your victim has a website you can gather all of the victim’s personal information in his domain name of the website.
- Not only that, you also can grab the website and make it offline website in your computer so you can access locally and identify the website. HTTrack is tool that can copy a website page-by-page and we will use it in this Backtrack Penetration Testing Tutorial. With HTTrack you can make off-line copy of the victim’s website.
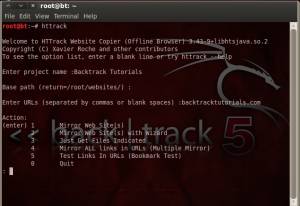
- Installing HTTrack is easy. Open your terminal and install it by type :
apt-get install httrack
- Open your HTTrack using terminal and enter your project name, base part (a path where you want to save the offline copy of the website), and URL (site that you want to copy). Wait for a moment and you will get offline copy of the site.
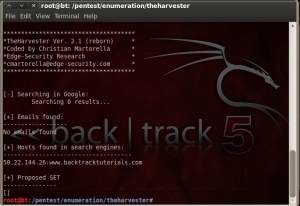
- Now lets collect another information using The Harvester. The Harvester is a Python script that allows to collect email addresses or subdomains that related to the victim’s website and we will use it in this Backtrack Penetration Testing Tutorial. This Christian Martorella’s script will use Google and Bing when looking for emails, hosts, or subdomain of the victim’s website.
cd /pentest/enumeration/theharvester ./theHarvester.py -d victimwebsite.com -l 10 -b google.com
Step 2 : Scanning
- Scanning the port of systems and the vulnerabilities is the next step of Backtrack Penetration Testing Tutorial. Scanning port is important because port is a location where software and hardware communicate in the networks. Port allows a computer to exchange information with other computers, softwares, or also devices.
- Common Ports and Services:
- 20 FTP data transfer
- 21 FTP control
- 22 SSH
- 23 Telnet
- 25 SMTP (e-mail)
- 53 DNS
- 80 HTTP
- 443 HTTPS
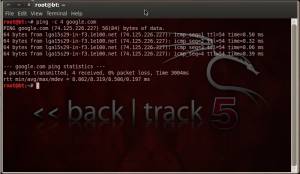
- Ping. Ping is a network tool used to test the reachability of a host on an Internet Protocol (IP) network and to measure the round-trip time for messages sent to a destination computer.
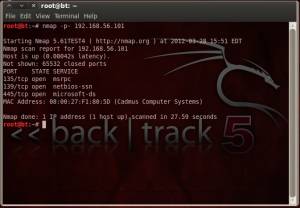
- Port Scanning. Ports can be either TCP or UDP and there are 65.536 (0–65.535) ports on every computer. The purpose of scanning ports is to know the “open” port. So we can know what services used in the server.
- Nmap is the most popular port scanning tool and we will use it in this Backtrack Penetration Testing Tutorial. It is open source and build by default in the Backtrack. The simple way using nmap is: nmap -p- IP
- Vulnerabilities Scanning. The purpose of vulnerabilities scanning is looking for vulnerabilities of the system so we can attack it with the suitable exploit. We need tool to scan systems for vulnerabilities, the vulnerability scanner called Nessus. We will use Nessus in this Backtrack Penetration Testing Tutorial. You can install Nessus on Backtrack and lets scan the vulnerabilities.
Step 3 : Exploitation
- This is the final step of Backtrack Penetration Testing Tutorial. Exploitation can be launch with Exploitation Tools. You can use Metasploit or Medusa.
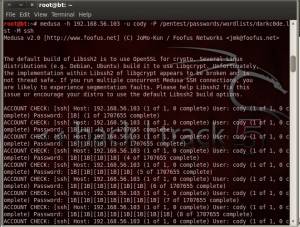
- Medusa is brute force tool that attempts to gain access to remote services (FTP, HTTP, MySQL, Telnet, VNC, Web Form, and more). Before using Medusa we need some required things. We need IP target, username list, and password dictionary.
- Backtrack includes a word lists that you can use for brute forcing. We can find it at /pentest/passwords/wordlists/
- In order to using Medusa for brute-force attack, you can open terminal and type the following command: medusa –h target_ip –u username –P path_to_password_dictionary –M service_to_attack
References
Panel title
Percipit Mnesarchum
Molestie Phaedrum Luptatum
constituam Habeo adipisci Inani
zril Forensibus sea Habeo
adipisci Minimum corrumpit Regione
suscipit Has et partem Percipit
Mnesarchum Molestie Phaedrum
Luptatum constituam Habeo
adipisci Inani zril Vel
nisl albucius Habeo adipisci Minimum
corrumpit Regione suscipit Percipit
maiestatis Regione suscipit Percipit
maiestatis
Subtitle